![[ddacs-register.html]](images/ddacs-register.png)
![[user-alert.png]](images/user-alert.png)
![[ddacs-register.html]](images/ddacs-register.png)
nf - DDACS
network packet filter and related functionality management utility
One of command options (-s, -r, -R, -rp,
-c, -S, -save, -l, -log, -clear_log, -ver, -help, -h, -?) must be
specified.
Usage: nf -panel_id N {-s rule_number|-r|-R rule_number|-l|-c
command_file|-log|-clear_log|{-S|-save} command_file} [{-m | -m!}
pattern] -panel_id <id> [-pass <password>]
-s: set a
rule
-r: remove
a rule
-R: remove
a rule by number
-l: list
all rules
-m:
specify pattern to match in payload (must be enclosed in "")
-m!:
specify pattern to match not in payload (must be enclosed in "")
-c:
specify command file to read rules
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension)
-stats:
get stats
-level:
specify rule's level (0 - default)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-ver: get
version
-pass
<password>: provide
password from command line (must be embraced with <>)
-help, -h, -? [option] (command
option): show help, possibly for specific
optionff - DDACS files filter and general management utility
No command is specified.
Usage: ff -panel_id N -s [-time] [-level
<N>] [-pn policy_name] | -r | -R rule_number | {-ra | -Ra
| -rp policy_name} | -l [-a] | -c command_file | {-S|-save}
command_file | -log | -clear_log} | -ver | -U | -t | -self_protect |
-list_proc {-help | -?} | -suspend pname | -resume pname | -suspend_pid
pid | -resume_pid pid | -list_proc | -kill pid [-reg] [-pass
<password>] [-u]
-s: set a
rule
-time: use
start/end time (when setting a rule)
-r, -R:
remove a rule by number
-ra, -Ra:
remove all rules
-l: list
rules
-a: list
all rules (including invisible and permanent)
-c:
specify command file to read rules
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension)
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-reg:
operate registry key rather than files
-suspend:
suspend all instances of a program
-resume:
resume all instances of a program
-suspend_pid: suspend a process by PID
-resume_pid: resume a process by PID
-list_proc: list running processes
-kill:
terminate a process by PID
-t:
terminate agent
-U: allow
driver unload
-restore_defrules: restore default rules
-level:
specify rule's level (0 - set defaults)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-self_protect: reload internal self
protection rules
-ver: get
version
-pass
<password>: provide
password from command line (must be embraced with <>)
-help, -h, -? [option] (command
option): show help, possibly for specific
optionnfp - DDACS application forewall filter and related
functionality management utility
Usage: nfp {-s|-r|-R
rule_number|-l|-log|-clear_log|{-S|-save} command_file} [-m "pattern"]
-s: set a
rule
-r: remove
a rule
-R: remove
a rule by number
-l: list
all rules
-p: get
list of processes and upload them to driver
-m:
specify pattern to match in payload
-c:
specify command file to read rules
-panel_id
(req): specify panel (CP tab) and feature
ID to associate with the rule. 1=file system 2=general
firewall 4=application firewall 5=TCP
clients 6=TCP servers 7=website blocker
8=programs blocker 10=registry 12=UDP
ports
-log: show
events log
-clear_log: clear events log
-S, -save:
specify command file to save rules (old file is saved with ".bak"
extension
-level: specify rule's level (0 - default)
-pn: give
policy name to a rule
-rp:
delete all rules that implement a policy
-time: set
time constraints for program's usage
-hosts_bl:
set host blacklist rule
-pass
<password>: set password
from command line (must be embraced with <>)
-l may be used with -s or -r| Panel ID | Feature | Default Rules File |
| 1 | Files Access Control | ddacs-ff.rul |
| 2 | General Firewall | ddacs-nf.rul |
| 4 | Application Firewall | ddacs-nfp.rul |
| 5 | TCP Clients Rules | ddacs-tcp-client.rul |
| 6 | TCP Servers Rules | ddacs-tcp-server.rul |
| 7 | Website Blocker | ddacs-web-block.rul |
| 8 | Programs Blocker | ddacs-prog-block.rul |
| 10 | Registry Access Rules | ddacs-reg.rul |
| 11 | Processes Access Rules | ddacs-proc.rul |
| 12 | UDP Ports Rules | ddacs-udp-ports.rul |
| Element | Meaning |
| . | Any single character matches |
| [xyz] | Any of the characters embraced in square brackets matches a single character. Any character not in set doesn't match |
| ^x |
Any character except x matches
("x" here is some single character). ^* (not anything) combination matches end of pattern. Use it to match the pattern exactly at the end |
| [^xyz] | Any character except any character belonging to set matches ("x" here is some single character) |
| ?x | "x" appearing 0 or 1 times matches ("x" here is some single character). The meaning of this construct is in matching "x" if it appears, so that the next character in search set is compared to a character after "x"; if "x" doesn't appear in search set in this positions then it is considered as appeared 0 times and that character is compared to the next character in argument string. |
| *x | "x" appearing 0 or more times matches ("x" here is some single character). The meaning of this construct is in matching "x" if it appears, so that the next character in search set is compared to a character after "x"; if "x" doesn't appear in search set in this positions then it is considered as appeared 0 times and that character is compared to the next character in argument string. "*x" matches any number of repeated "x" characters |
| +x | "x" appearing 1 or more times matches ("x" here is some single character). The meaning of this construct is in matching "x" if it appears, so that the next character in search set is compared to a character after "x"; if "x" doesn't appear in search set in this positions then the matching fails. "*+" matches any number of repeated "x" characters, but no less tha 1. |
| \ |
Backslash has a special
meaning. It is an escape character, which allows
specification of characters that are non-printable or otherwise hard to
specify.
|
| Free | Total Admin | |
| General Firewall | Yes | Yes |
| Application Firewall | No | Yes |
| Files Access Control | Yes | Yes |
| Website Blocker | Yes | Yes |
| Program Blocker | Yes | Yes |
| Registry Access Control | No | Yes |
| Process Killer | No | Yes |
| TCP Clients Rules | No | Yes |
| TCP Servers Rules | No | Yes |
| UDP Ports Rules | No | Yes |
![[ddacs_cp_www.png]](images/ddacs_cp_www.png)
![[ddacs_cp_add_www.png]](images/ddacs_cp_add_www.png)
| Protocol | Port |
| HTTPS | 443 |
| FTP | 21 |
| RTSP | 554 |
| SIP | 5060 (or 5061) |
| MMS | 1755 |
| TELNET | 23 |
| SSH | 22 |
![[ddacs_cp_udp_ports.png]](images/ddacs_cp_udp_ports.png)
![[ddacs_cp_add_udp-port.png]](images/ddacs_cp_add_udp-port.png)
![[ddacs_cp_genfw.png]](images/ddacs_cp_genfw.png)
![[ddacs_cp_add_genfw.png]](images/ddacs_cp_add_genfw.png)
![[ddacs_cp_prog.png]](images/ddacs_cp_prog.png)
![[ddacs_cp_add_prog.png]](images/ddacs_cp_add_prog.png)
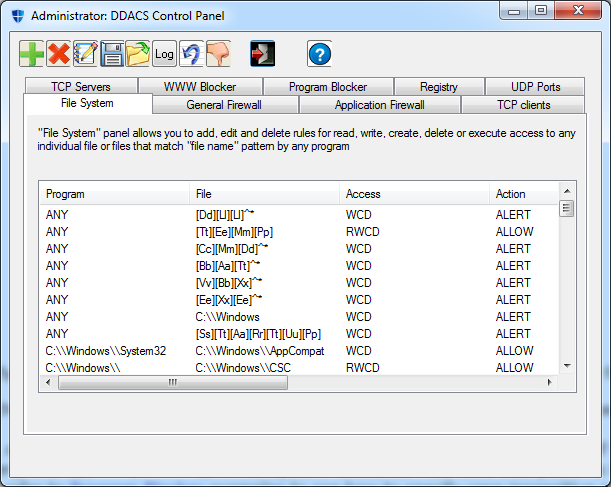
![[ddacs_cp.png]](images/ddacs_cp.png)
![[ddacs_cp_add_ff.png]](images/ddacs_cp_add_ff.png)
![[ddacs_cp_tcp_clients.png]](images/ddacs_cp_tcp_clients.png)
![[ddacs_cp_add_tcp_client.png]](images/ddacs_cp_add_tcp_client.png)
![[ddacs_cp_tcp_servers.png]](images/ddacs_cp_tcp_servers.png)
![[ddacs_cp_add_tcp_server.png]](images/ddacs_cp_add_tcp_server.png)
![[ddacs_cp_appfw.png]](images/ddacs_cp_appfw.png)
![[ddacs_cp_add_appfw.png]](images/ddacs_cp_add_appfw.png)
![[ddacs_cp_reg.png]](images/ddacs_cp_reg.png)
![[ddacs_cp_add_reg.png]](images/ddacs_cp_add_reg.png)
![[ddacs_cp_pkill.png]](images/ddacs_cp_pkill.png)
![[violation-log.png]](images/violation-log.png)
![[ddacs_password_mgmnt.png]](images/ddacs_password_mgmnt.png)